Pod API modify body
Introduction
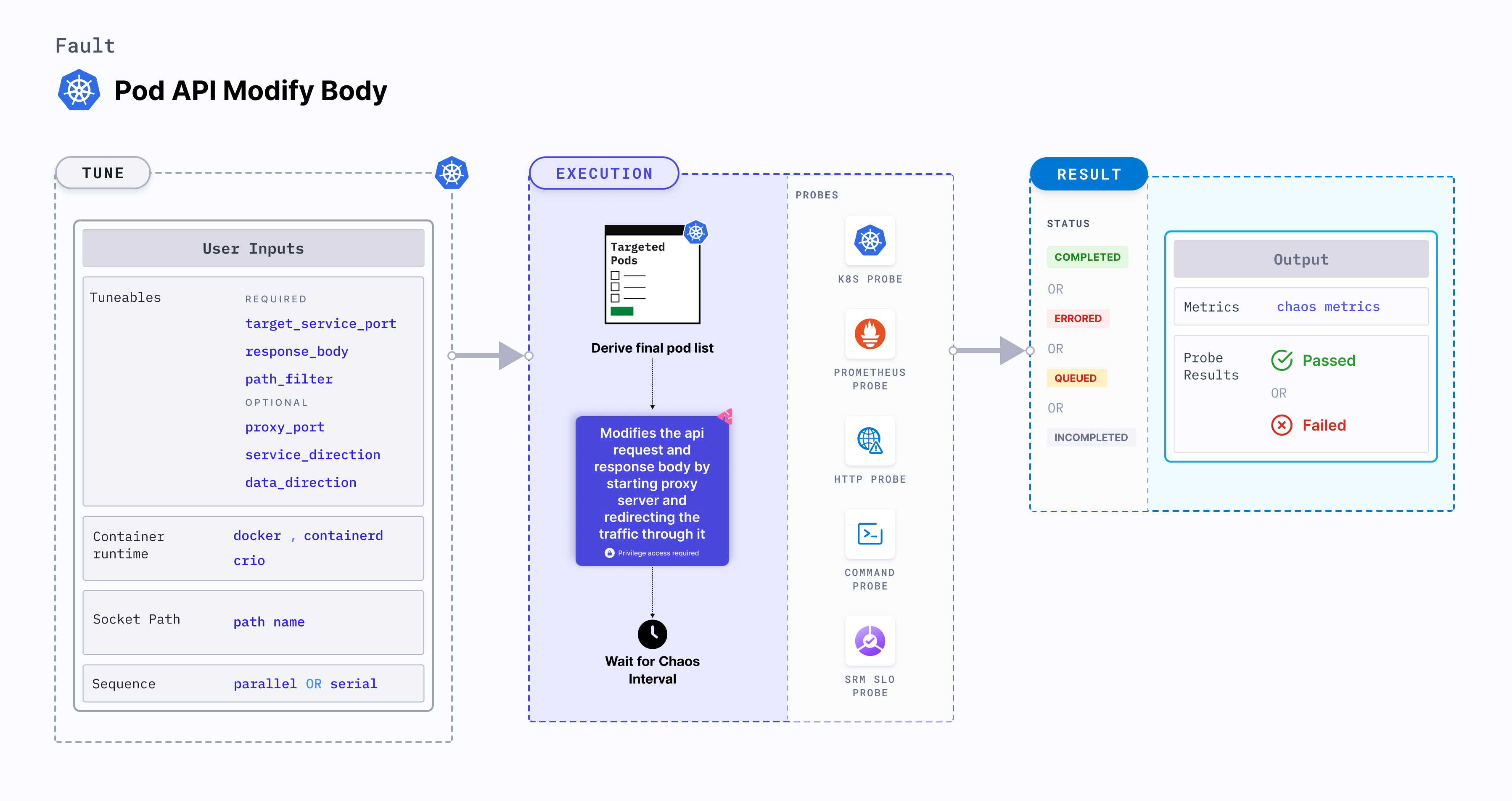
Pod API modify body is a Kubernetes pod-level chaos fault that modifies the api request and response body by replacing any portions that match a specified regular expression with a provided value. This is achieved by starting the proxy server and redirecting the traffic through the proxy server.
Use cases
Pod API modify body:
- It can be used for API testing, by replacing specific portions of the request or response body to simulate different scenarios and validate how your application handles different data variations.
- Simulate error conditions and test the error handling capabilities of API by replacing specific patterns in the response body with error messages or custom error codes to test error handling and reporting mechanisms are in place.
- It can be useful for obscuring or redacting personally identifiable information (PII), such as email addresses or phone numbers, before logging or transmitting the data for security and privacy compliance.
- Kubernetes> 1.17 is required to execute this fault.
- The application pods should be in the running state before and after injecting chaos.
Fault tunables
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| TARGET_SERVICE_PORT | Port of the target service. | Defaults to port 80. For more information, go to target service port |
| RESPONSE_BODY | String body to overwrite the HTTP response body. | If no value is provided, response will be an empty body. Defaults to empty body. For more information, go to response body |
| PATH_FILTER | Api path or route used for the filtering | For more information, go to path filter |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| PROXY_PORT | Port where the proxy listens for requests. | Default: 20000. For more information, go to proxy port |
| SERVICE_DIRECTION | Direction of the flow of control, ingress or egress | Default: `ingress`. For more information, go to service direction |
| DATA_DIRECTION | API payload type, request or response | Default: `both`. For more information, go to data direction |
| NETWORK_INTERFACE | Network interface used for the proxy. | Default: `eth0`. For more information, go to network interface |
| CONTAINER_RUNTIME | Container runtime interface for the cluster | Default: containerd. Support values: docker, containerd and crio. For more information, go to container runtime |
| SOCKET_PATH | Path of the containerd or crio or docker socket file. | Default: /run/containerd/containerd.sock. For more information, go to socket path |
| TOTAL_CHAOS_DURATION | Duration of chaos injection (in seconds). | Default: 60 s. For more information, go to duration of the chaos |
| TARGET_PODS | Comma-separated list of application pod names subject to pod HTTP modify body. | If not provided, the fault selects target pods randomly based on provided appLabels. For more information, go to target specific pods |
| PODS_AFFECTED_PERC | Percentage of total pods to target. Provide numeric values. | Default: 0 (corresponds to 1 replica). For more information, go to pod affected percentage |
| RAMP_TIME | Period to wait before and after injecting chaos (in seconds). | For example, 30 s. For more information, go to ramp time |
| SEQUENCE | Sequence of chaos execution for multiple target pods. | Default: parallel. Supports serial and parallel. For more information, go to sequence of chaos execution |
Target service port
Port of the targeted service. Tune it by using the TARGET_SERVICE_PORT environment variable.
The following YAML snippet illustrates the use of this environment variable:
## provide the port of the targeted service
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-api-modify-body
spec:
components:
env:
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
# provide the body string to overwrite the response body
- name: RESPONSE_BODY
value: "/.+/test"
- name: PATH_FILTER
value: '/status'
Response body
String body that overwrites the API request and response body. Tune it by using the RESPONSE_BODY environment variable.
The following YAML snippet illustrates the use of this environment variable:
## provide the response body value
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-api-modify-body
spec:
components:
env:
# provide the body string to overwrite the response body
- name: RESPONSE_BODY
value: "/.+/test"
- name: PATH_FILTER
value: '/status'
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
Path Filter
API sub path/route to filter the api calls. Tune it by using the PATH_FILTER environment variable.
The following YAML snippet illustrates the use of this environment variable:
## provide api path filter
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-api-modify-body
spec:
components:
env:
# provide the api path filter
- name: PATH_FILTER
value: '/status'
- name: RESPONSE_BODY
value: "/.+/test"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
Destination ports
A comma-separated list of the destination service or host ports for which egress traffic should be affected as a result of chaos testing on the target application. Tune it by using the DESTINATION_PORTS environment variable.
It is applicable only for the egress SERVICE_DIRECTION.
The following YAML snippet illustrates the use of this environment variable:
## provide destination ports
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-api-modify-body
spec:
components:
env:
# provide destination ports
- name: DESTINATION_PORTS
value: '80,443'
# provide the api path filter
- name: PATH_FILTER
value: '/status'
- name: RESPONSE_BODY
value: "/.+/test"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
HTTPS enabled
This item is employed to facilitate HTTPS for both incoming and outgoing traffic, and its usage can vary depending on whether it's applied to ingress or egress scenarios. Tune it by using the HTTPS_ENABLED environment variable.
When applied to
ingresstraffic, it should be configured astrueif the HTTPS URL of the target application includes a port, following the formathttps://<hostname>:port. However, for HTTPS URLs in the form ofhttps://<hostname>without a port, this setting is not required.For egress traffic, setting it to
trueis necessary to enable HTTPS support for external services, which will then establish TLS certificates for the proxy within the target application.
The following YAML snippet illustrates the use of this environment variable:
## enable https support
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-api-modify-body
spec:
components:
env:
# enable https support
- name: HTTPS_ENABLED
value: 'true'
# provide the api path filter
- name: PATH_FILTER
value: '/status'
- name: RESPONSE_BODY
value: "/.+/test"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
Advanced fault tunables
PROXY_PORT: Port where the proxy listens for requests and responses.SERVICE_DIRECTION: Direction of the flow of control, either ingress or egress. It supportsingress,egressvalues.DATA_DIRECTION: API payload type, request, or response. It supportsrequest,response, andbothvalues.NETWORK_INTERFACE: Network interface used for the proxy.
The following YAML snippet illustrates the use of this environment variable:
# it injects the api modify body fault
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-api-modify-body
spec:
components:
env:
# provide the proxy port
- name: PROXY_PORT
value: '20000'
# provide the connection type
- name: SERVICE_DIRECTION
value: 'ingress'
# provide the payload type
- name: DATA_DIRECTION
value: 'both'
# provide the network interface
- name: NETWORK_INTERFACE
value: 'eth0'
# provide the api path filter
- name: PATH_FILTER
value: '/status'
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
- name: RESPONSE_BODY
value: "/.+/test"
Container runtime and socket path
The CONTAINER_RUNTIME and SOCKET_PATH environment variable to set the container runtime and socket file path, respectively.
CONTAINER_RUNTIME: It supportsdocker,containerd, andcrioruntimes. The default value iscontainerd.SOCKET_PATH: It contains path of containerd socket file by default(/run/containerd/containerd.sock). Fordocker, specify path as/var/run/docker.sock. Forcrio, specify path as/var/run/crio/crio.sock.
The following YAML snippet illustrates the use of these environment variables:
## provide the container runtime and socket file path
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-api-modify-body
spec:
components:
env:
# runtime for the container
# supports docker, containerd, crio
- name: CONTAINER_RUNTIME
value: "containerd"
# path of the socket file
- name: SOCKET_PATH
value: "/run/containerd/containerd.sock"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
# provide the api path filter
- name: PATH_FILTER
value: '/status'
- name: RESPONSE_BODY
value: "/.+/test"