Targets, baselines, and variants in STO
Every scan step has a specific target, which is a user-defined label for the code repository, container, application, or configuration to scan. You define the test target when you configure the scan step. It is good practice to create descriptive, specific labels for your scan targets.
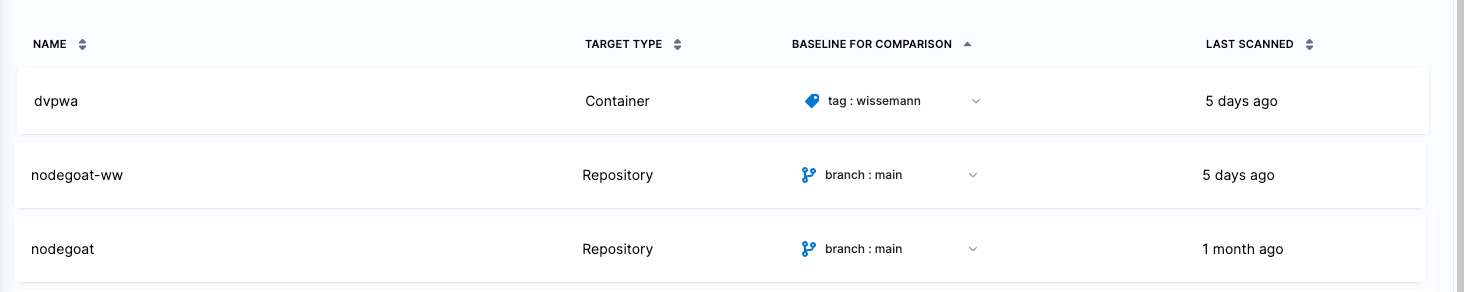
You can view all your targets in one page: go to Security Tests (left menu) and then Test Targets.
Each scan operation has a specified variant that specifies the branch, tag, or other target variant to scan.
You can also specify a baseline for each target. This is usually the "root" variant of the target, such as the main branch or the latest tag. When a scan finishes successfully, STO does the following:
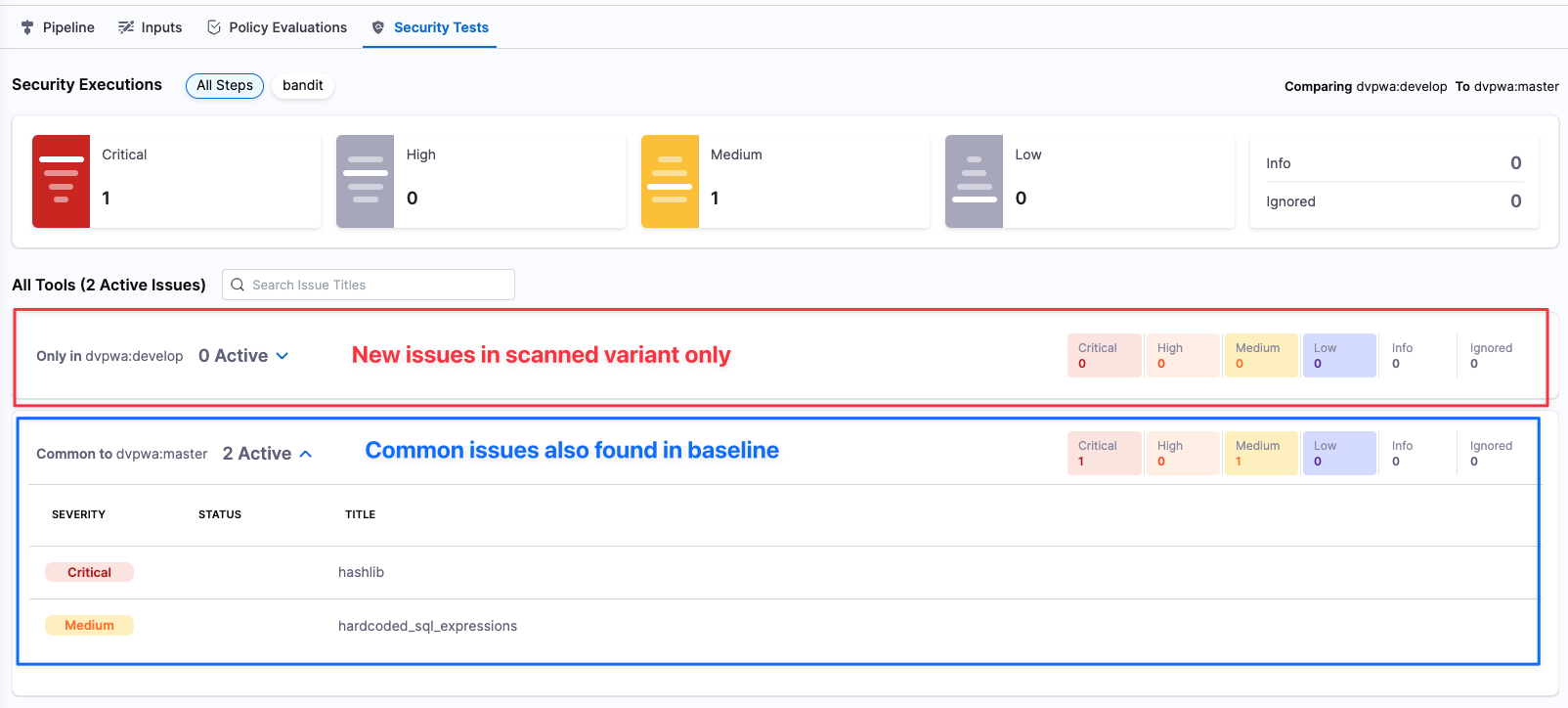
- Compares each issue detected in the scanned variant against the target baseline.
- Places each issue into one of two buckets:
- "New" issues in the current variant only, or
- "Common" issues also in the baseline (or, if no baseline is specified, in the previous scan).
It is good practice to specify a baseline for every target, for the following reasons. To define your baselines, go to Security Tests (left menu) > Test Targets. Each target has a Baseline for Comparison menu.
For developers, it’s critical to distinguish between security issues in the baseline vs. issues in the variant you’re working on. Thus if you’re working in a downstream branch, you want to detect and resolve issues in your branch (the variant) before merging, so you don’t introduce them into the main branch (the baseline).
When you scan a variant of a target with a baseline defined, the scan results make it easy to identify issues in the variant only (“your” issues) vs. issues also found in the baseline.
The STO Overview and Security Testing Dashboard show detected issues for targets with baselines defined. While individual scan results focus on variant issues, these views focus on baseline issues. These views enable security personnel and other non-developers to monitor, investigate, and address issues in production-ready targets and view vulnerability trends over time.
In short, defining a baseline makes it easy for developers to drill down into “shift-left” issues in downstream variants and security personnel to drill down into “shift-right” issues in production targets.
You can easily identify new vs. common issues in the results for each scan.