Connect to ServiceNow
You can connect Harness to ServiceNow using a Harness ServiceNow connector. This connector allows you to approve and reject pipeline steps.
Important notes
- Your ServiceNow account should ideally have the
adminrole. If this is not possible, it should have at least theitil_adminoritilrole to create and modify tickets. - Your account should also have the
import_adminorimport_transformerrole to manage import set transform maps. For details, go to ServiceNow's Base System Roles documentation. - Your ServiceNow REST API account must have permission to view tickets.
Add a ServiceNow connector
This topic assumes you have a Harness Project set up. If not, go to Create Organizations and Projects.
You can add a connector from any module in your project in project setup, or in your organization, or account resources.
This topic shows you how to add a ServiceNow connector to your project.
In Project Setup, select Connectors.
Select New Connector, and then select ServiceNow. The ServiceNow connector settings appear.
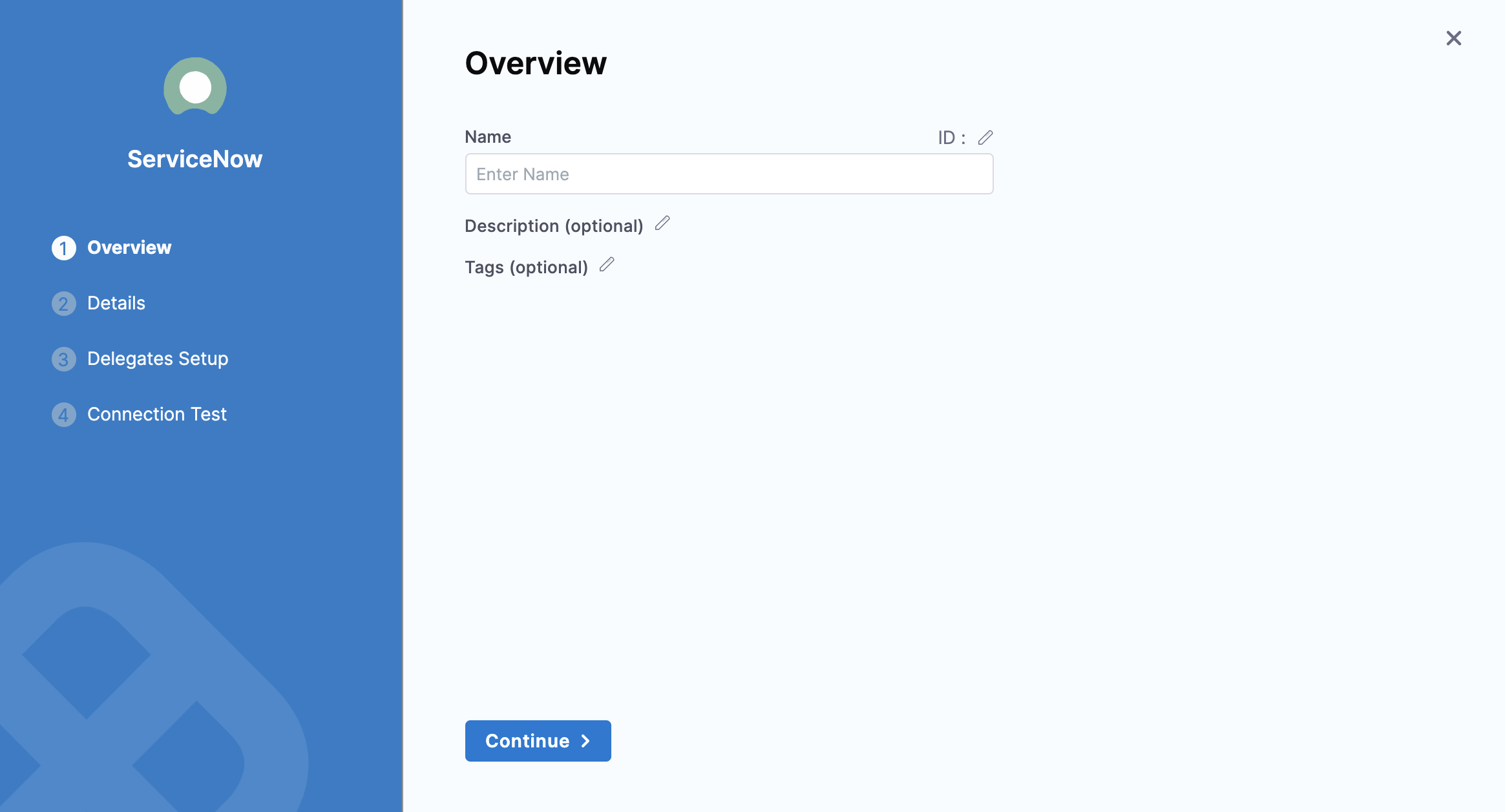
Enter Name for this connector.
You can choose to update the Id or let it be the same as your ServiceNow connector's name. For more information, go to Entity Identifier Reference.
Enter a Description and Tags for your connector.
Select Continue.
Add details for the ServiceNow connector
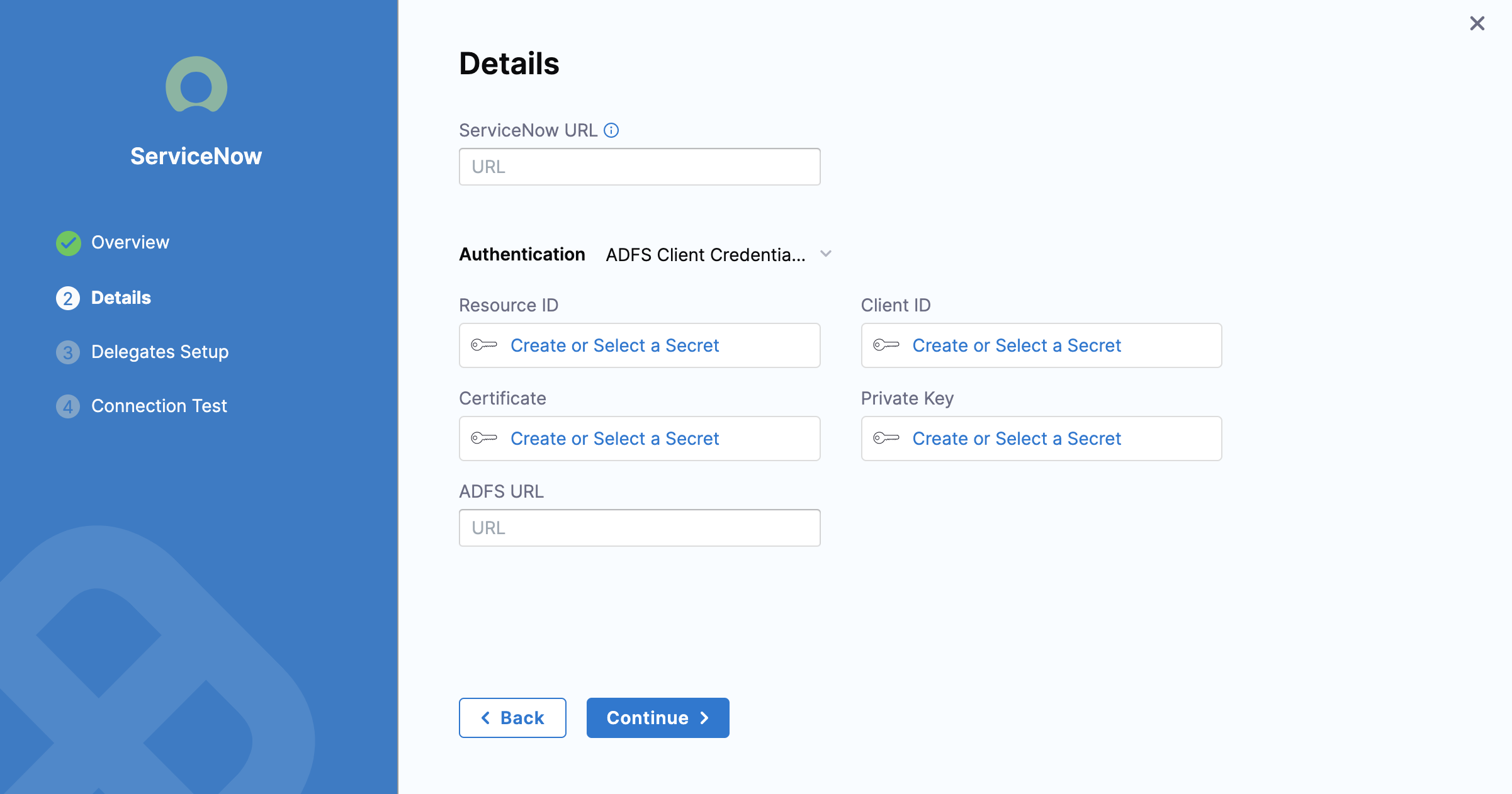
In ServiceNow URL, enter the base URL by which your users will access ServiceNow. For example:
https://example.service-now.com.In Authentication, select one of the following:
- Username and Password
- ADFS Client Credentials with Certificate
- OIDC Refresh token
- Username and Password
- ADFS Client Credentials with Certificate
- OIDC Refresh token
To use a username and password for authentication, do the following:
- Enter Username.
- In Password/API Key, create a new password or API key or enter an existing one. For API Key, use a Harness Text Secret.
- Select Continue.
- For information on client credentials with certificates, go to the AD FS OpenID Connect/OAuth flows and Application Scenarios.
- Harness supports private keys encoded in RSA (in PKCS8 format).
- Harness supports certificates in
X509format. - Permissions granted to this connector in ServiceNow depend on the configuration of the client application group.
To use ADFS credentials for authentication:
Select an existing secret or create one that has the resource identifier of ServiceNow configured in ADFS as its value for the Resource ID field.
Select an existing secret or create one that has the application (client) id assigned to your application by AD FS for the Client ID field.
Select an existing encrypted file or create one that has the certificate for the Certificate field. This is a
X509format certificate used for signing JWT tokens by your application.In Private Key, create a new secret or choose an existing one that has the AD FS private key as the value. This key is the private RSA key corresponding to certificate uploaded in the Certificate field.
In ADFS URL, enter the base AD FS URL.
This feature requires Harness Delegate 799xx or higher.
Harness supports persistent refresh tokens only to authenticate via OpenID Connect (OIDC) for a Refresh Token with a Grant Type of refresh_token. For more information on refresh token grant types, go to Refreshing Access Tokens in the OAuth documentation.
All refresh tokens must be valid and updated when revoked. Permissions granted in ServiceNow to this connector depend on the associated resource owner for the credentials/refresh token.
To use an OIDC refresh token for authentication, do the following:
Select an existing secret or create one that has the application (client) ID assigned to your application by OIDC for the Client ID field.
Optional: Select an existing secret or create one that has the application (client) secret assigned.
Create a secret for the Refresh Token.
Enter the explicit Token URL. For example:
- ServiceNow authentication server:
https://<YOUR_DOMAIN>.service-now.com/oauth_token.do - Okta authentication server:
https://<YOUR_DOMAIN>.okta.com/oauth2/v1/token
- ServiceNow authentication server:
(Optional) Enter the Scope. If you use ServiceNow for your authentication server, the Scope is not required. Harness fetches it from the ServiceNow URL.
To learn more about how to configure scope for a client in ServiceNow, go to REST API Auth Scope in the ServiceNow documentation.
Select Continue.
Set up delegates
Select the Harness Delegate(s) to use when making a connection to ServiceNow using this connector.
Select Save and Continue.
Harness tests the connection.
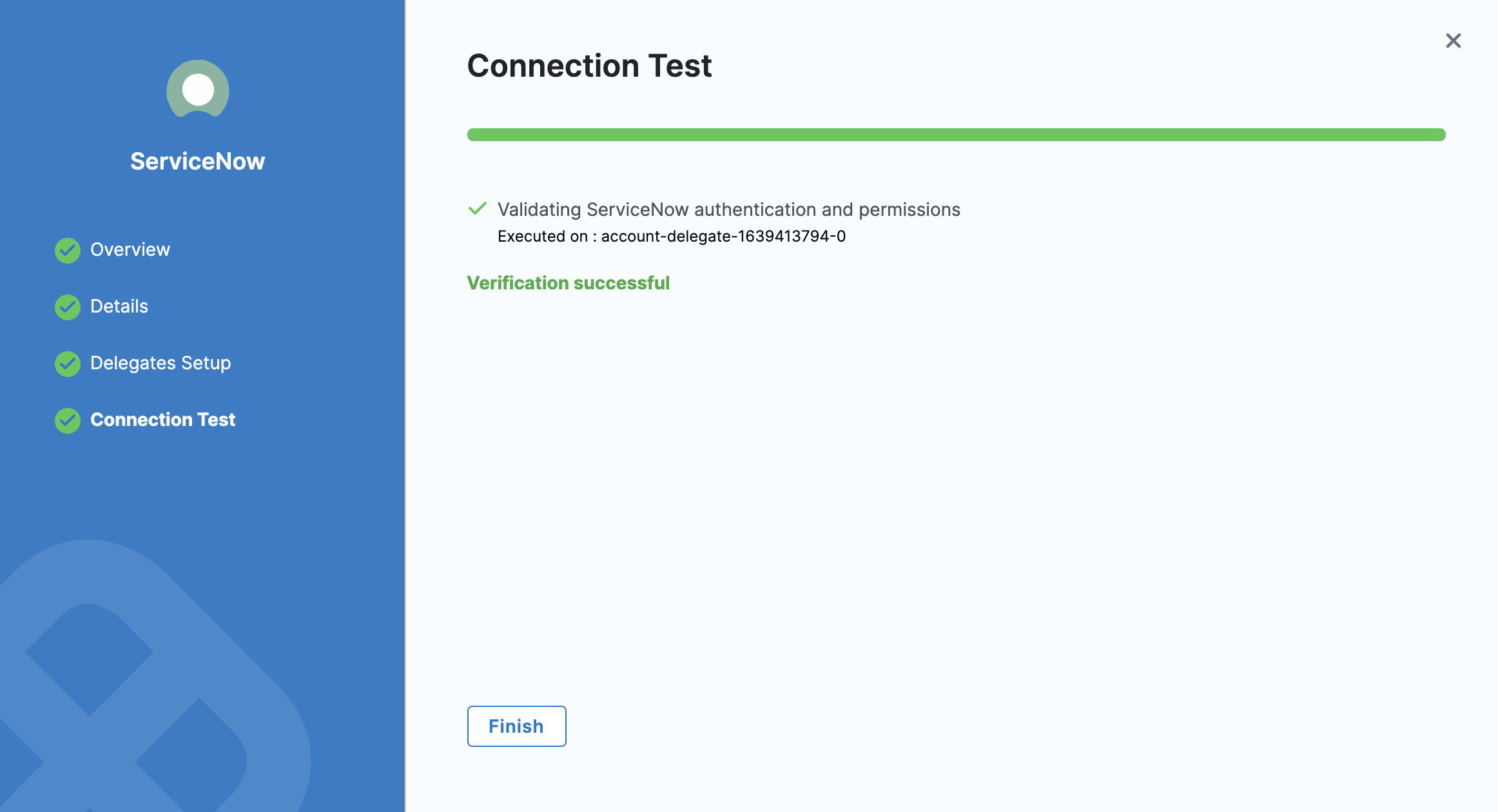
Select Finish.
The ServiceNow connector is listed in Connectors.